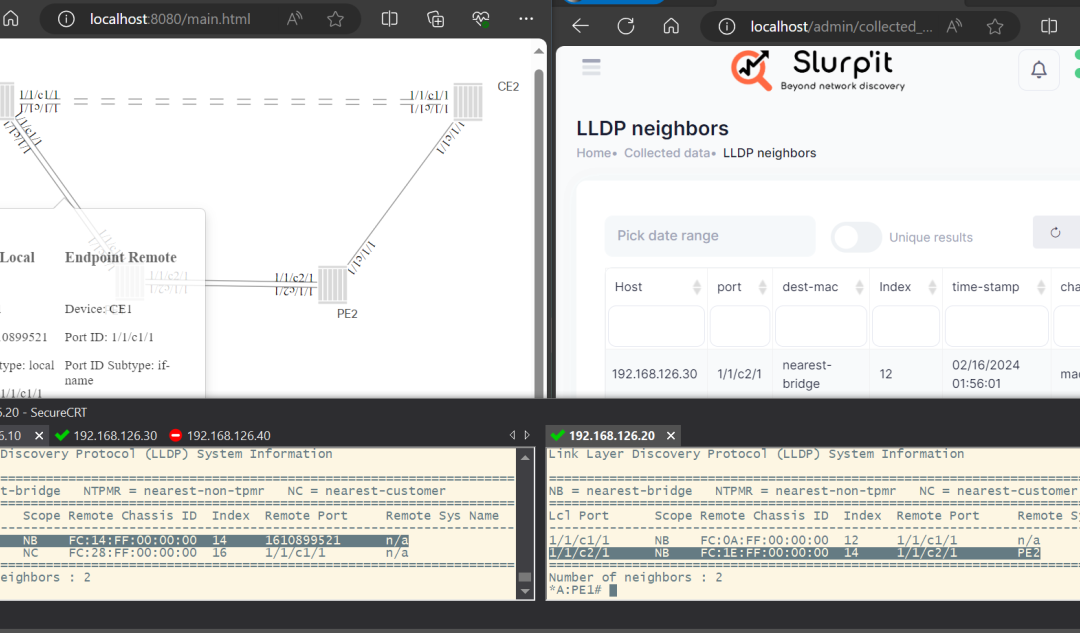
Sluggish connection is something most businesses won’t like to hear about. And this can happen through anything – bandwidth logs, misconfigured routers, or because of some rogue app update.
But did you ever believe it can even happen through a switch that was there in the server room unpatched, unsecured, and unaccounted for?
One overlooked device can cause a real domino effect to any business. This usually happens when the business doesn’t know what’s there on their network as per Slurp’it. And that’s exactly where network device discovery comes to the escape, and become a foundational piece to asset lifecycle management. Let’s understand in detail below, how!
Why is visibility important?
IT environments now are more complex than ever. There are remote users, hybrid cloud, mobile devices, IoT, third party apps – alot to see and management. Apart from this complexity, there are even routers attached, switches, firewalls, printers, and IP phones.
Network device discovery gives businesses the control. They get to check out their complete infrastructure. They can identify each device, based on the type, location, configuration, and also status.
With this visibility – businesses know what’s connected or where – and they can thus easily manage, secure, and support it all as per Slurp’it.
What is asset lifecycle management?
Let’s first understand Asset Lifecycle Management first. Starting from the moment the asset enters the network to the moment it retires.
The whole process looks like:
1. Procurement, getting the right equipment, the right time
2. Then deployment. Installing and configuring all the devices
3. Next operation. Keeping all the devices updated. Everything should regularly be monitored throughout.
4. Maintenance.
5. Lastly, disposal.
How network device discovery supercharges ALM?
We will break down the whole thing into each stage of lifecycle management.
Procurement
Most of the businesses out there grow in an ad hoc way. There could be new devices here, upgrades somewhere else, and replacements elsewhere.
Without network device discovery, onboarding any new assets gets difficult, or maybe more like a guessing game. Businesses will now know what’s actually on their network. They would not understand what needs replacing, and everything will get more tedious as per Slurp’it.
With automated device discovery businesses can
● Detect new devices instantly
● Get real time information
● Match all the assets against policies
● Add them to their inventory quickly
With this, businesses actually start with clarity and not chaos.
Operations
For example, your router in the office somehow goes off during peak hours. Or maybe a switch port gets overloaded. If you as a business are unaware of where it’s located or what’s connected to it, troubleshooting gets difficult here.
With network device discovery businesses can
● See all the live topologies
● Check out the performance stats
● Track device uptime and configuration changes
● Quickly isolate all the failing nodes and reroute the whole traffic
With the insights the business will get here, the network runs smoothly.
Compliance
No matter in what industry you are in – be it healthcare, finance, or something else, you will need to know:
● What devices exist in the system
● Where they are located
● Who is using them
● Whether they are compliant or not
Network device discovery actually does all the heavy lifting. It integrates with CMDB’s and ITSM platforms smoothly.
Lifecycle Management
Next up lifecycle management. Over time some devices may get obsolete. But if a business don’t have the visibility, all the aging assets stay hidden.
It actually helps with:
● Which devices are past their end of life
● Which assets are underutilized
● Which ones are nearing warranty expiration
● Where hardware performance is degrading
With this knowledge, businesses can
● Plan upgrades in advance
● Avoid all the unnecessary purchase
● Decommission safely and securely
● Keep total cost of ownership under control
How network device discovery strengthens security posture?
The tool keeps a check on outdated patches.
Also the tool monitor open ports. If there is any unusual traffic pattern or rogue configuration the device instantly highlights this up. And lastly, the tool even keeps a check on security baselines as per Slurp’it. This is done by comparing live device data against policy.
Some common pitfalls and how to avoid them all!
Given all the benefits, there are even a lot of pitfalls that’s there, but some common ones are:
● One time scan is just not enough
● Lack of integration with ALM or CMDB tools
● If there’s no proper clarification, asset inventory can turn to a messy game.
How to use network device discovery for ALM success?
Lastly, make sure that you can automate everything that you can. Try linking discovery to business intelligence. Make sure to train your team. And also build security policies on discovery data. Remember, if your network is a busy airport, network device discovery is our control tower. For more information, contact us at Slurp’it!