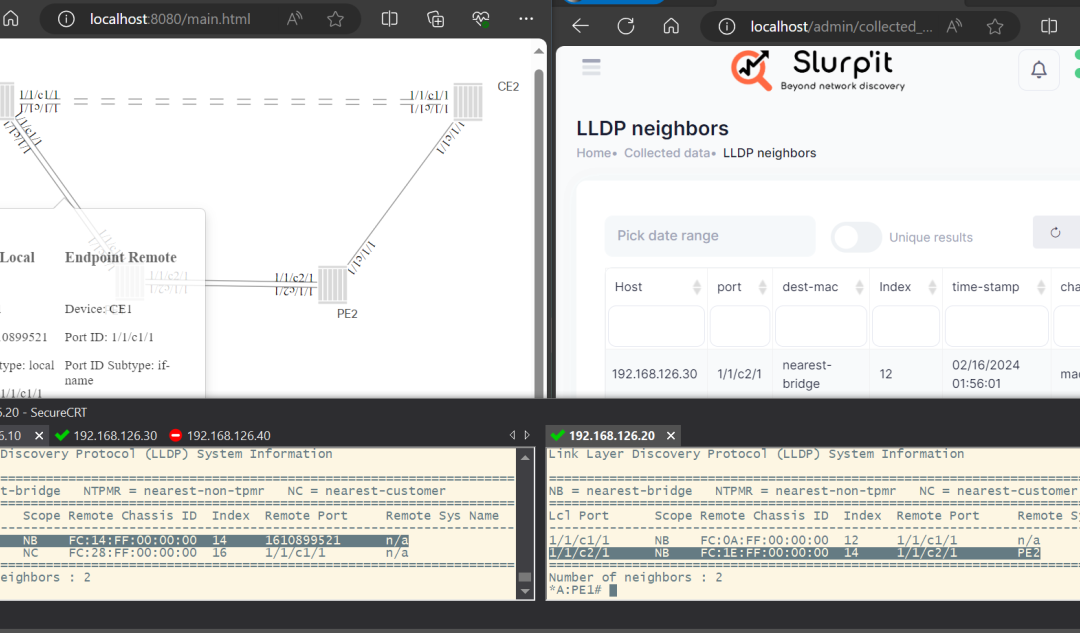
The business of now, and the instability around demands visibility. One has to know who’s inside their perimeter. Whether they are supposed to be there or not? Without all this information, the business flies blind, and that’s how breaches happen.
Let’s talk about the breach that happened very recently!
There was this mid-sized financial services firm. Recently they suffered a $2.3 million loss due to a data breach.
How?
There was a printer, a network connected printer. The printer came with an outdated firmware. It actually then became an open door for hackers. This printer was active on the network for years but never showed up on their security radar as per Slurp’it.
Why? Because they weren’t actively using this tools.
That printer was an invisible asset. And invisible assets actually interest hackers a lot.
What is network discovery, anyway?
Let’s come to the main part. What exactly is it? The complete process of automatically identifying all the devices connected to a network – is what network discovery means. It’s a census actually for the complete IT infrastructure as per Slurp’it.
These tools scan:
- All the computers and servers
- Mobile devices
- IoT devices like smart TVs or cameras
- Network hardware (switches, routers, printers)
- Cloud instances
These tools even scan the complete shadow IT assets too. It can check out the systems or devices operating without explicit organizational approval as per Slurp’it.
Good network discovery tools also provide context. Now what does that mean? You will get access to location, owner, OS, open ports, and even running services too as per Slurp’it.
How network discovery stops data breaches before they start?
Let’s understand the process first. How these tools actually work:
One of the major concerns for businesses of today is shadow IT. It can either be devices or some softwares that are deployed without the knowledge of the IT team. Maybe someone would have set up a rogue wifi router or might have installed some unauthorised software.
What these tools actually do here, is it finds shadow elements instantly. After discovery, IT teams can then isolate or evaluate them securely and remove them.
Next up, if there is any outdated software or devices that’s there in your infrastructure, these tools will give you a real time update of all the endpoints. The tool will actually allow businesses to push timely updates and patches wherever needed.
These tools also flag the activities that are alarming. For example, someone plugged in their personal laptop to the network. The tool will flag the device the moment they connect. Businesses get real time alerts, and the security team then can spring into action. They can either isolate the device, notify users, or disable the port remotely.
Lastly, we know that zero trust security is the new normal. Assuming there is no device or user that’s trustworthy. Once the business decides to enforce zero trust, they first need to have a complete view of their network. They should know all the devices and connection points. Further, they can create micro-segmented access rules, assign appropriate trust levels, and put in strict identity verification policies.
The benefits of network discovery you won’t want to miss!
Whether malicious or accidental, these tools are of great help for everything that’s dangerous to a business. Some may come from within. Some would already have a level of access. And here’s how it helps with all:
- Let’s say there’s an employee from HR. He/she suddenly starts accessing engineering servers late at night. That’s suspicious. These tools integrated with behavior analytics can flag such anomalies. Even if the user technically has access, which actually is a good thing.
- Next up, what if a usually benign device suddenly starts communicating with unknown external IPs? That’s problematic right. It tracks all the communication flows. It then flags deviations.
- A lot of advanced network discovery tools provide visual maps. Also some give access to heatmaps of user and device activity. These give IT admins access to track all the problematic activities
- Lastly, role based access auditing. Businesses can cross reference discovered devices with access controls. They can check out if someone has more permissions than they should. They can also shut down the access.
Some best practices to maximize network discovery for security
Know that, just having a tool isn’t enough. Here’s how you can make the most out of the network discovery tools you have to reap extra benefits:
- Make sure to schedule regular scans. Don’t ever rely on one time scans. You can try out automated, recurring scans to keep your inventory up-to-date.
- You can also feed discovery data into your Security Information and Event Management (SIEM) or Security Orchestration and Automation (SOAR) platforms for better threat related intelligence.
- Always track when devices are added, moved, updated, or removed. Make sure to decommission old devices properly and keep the inventories clean.
- Make it a habit to label devices by function. You can even do it department, or owner wise to make tracking and auditing easier.
- Lastly, educate employees. Run awareness programs. Explain the importance of authorised device use.
Here are a few more reasons why every organisation must consider network discovery, now!
Cybercriminals are no longer focusing solely on high-profile targets. SMEs, schools, hospitals. Know that, everyone’s a target. In fact, 60% of small businesses close within six months of a data breach.
It gives organizations of all sizes the edge by:
- Giving complete visibility
- Speeding up incident response
- Making compliance easier (GDPR, HIPAA, PCI-DSS)
- Helping best with security posture
And in a world where the average cost of a breach is $4.45 million (according to IBM), investing in Network Discovery isn’t just smart, it’s necessary. Don’t you all think so? For more information, contact us at Slurp’it!